Since we all are stucked at our homes due to the COVID-19. Soto maintain our work and studies students are using Zoom video conferencing to communicate with the class. Zoom got more popularity in these Quarantine days for remote video conferencing and seems to be offering a lot. Prime Minister of the UK Boris Johnson who was tested positive for COVID-19 , So we can guess it’s popularity that Boris Johnson conducted his first ever digital cabinet meeting and shared a screenshot of the same on twitter. He raised a security concerns on Tuesday 31 March 2020 when he tweeted a picture of cabinet meeting but did not hide the meeting ID number.
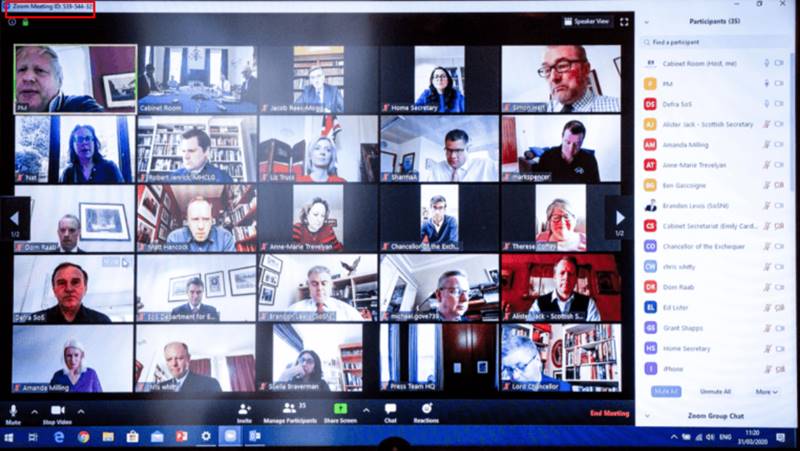
Boris shared the screenshot on twitter and wrote, ” This morning I chaired the first-ever digital Cabinet. Our message to the public is: stay at home, protect the NHS, save lives. #StayHomeSaveLives.”
However , the people on Twitter immediately noticed that the Boris Johnson had left the Zoom meeting ID number in the screenshot, as well as the usernames of ministers taking part. So after figuring out the meeting ID, many people attempted to crash into the meeting but it was password protected. And Zoom meetings keep getting hacked, that shone a Spotlight on the company’s security protections and privacy. The FBI’s Boston office reported last week that “Zoom bombing” incidentsare occurring across America.
Read more: WhatsApp Multiple Devices Support Feature and more launching soon.
This security issue has been exploited by hackers, with disturbing results. On March 30, uninvited strangers crashed a Zoom meeting on cyberattacks. When the presenter started covering the coronavirus disinformation posted to Reddit, Facebook, and Twitter, a Zoom bomber writes all over the screen, and forcing the meeting to end early.
Are you using Zoom? Make sure you go through this to ensure your privacy & security as Zoom isn’t taking care of yours. Risking more than 10 million users through high severity vulnerabilities.”If you care about your security and privacy, perhaps stop using Zoom – Researchers said.
So here an interesting question appears in our minds.
How does it works? and how can we save ourselves from getting HACKED?
When sending a chat message, any URLs are converted into hyperlinks so that other people can easily click it and directly go to the webpage, but the problem is that the Zoom client for windows doesn’t validate the paths and lead Windows networking UNC paths into a clickable link in the chat messages as well.
Example: C:\Windows\Firmware can be sent to the chatbox as \\127.0.0.1\C$\Windows\Firmware
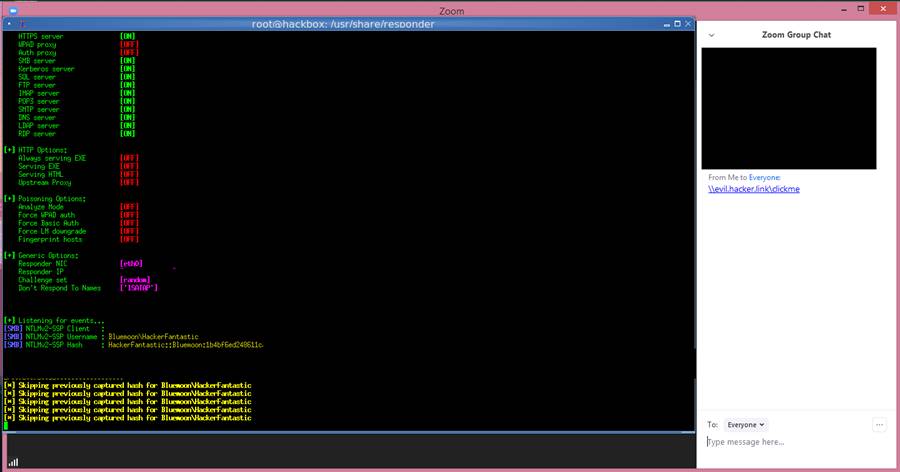
If any user clicks on path link, Windows will attempt to connect the remote site using the SMB file sharing protocol to open the remote file. When you doing this , by default Windows will send the user’s login name and their NLTM password hash, which can be cracked easily by using free tools like Hashcat to dehash.

if you see these kind of links then do not click on it , otherwise your system will be hacked.
Written By Sana Mansoor
Read more: Skype Meet Now feature introduced to rival Zoom.
Follow INCPAK on Facebook / Twitter / Instagram for updates.